How to add a shellcode generator or function or encode module ?
Main commands will be add in core/command.py on [line 13] commands = { #commands section.
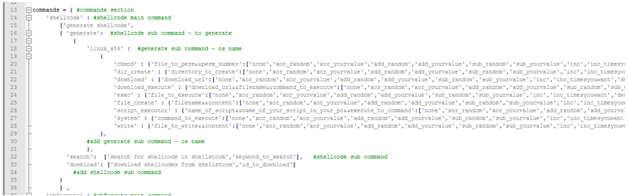
Note: if the texts are so small to view, please just open the core/command.py and see codes for explaining.
There is a shellcode which is a main command, and has a description, and then 3sub commands named generate , search and download.
In generate section we have another sub-command which is linux_x86, if you want add an OS, here is the place. Structure of new OS MUST be same as linux_x86 as explained here.
Next section is function lists, chmod,dir_create …write, and each of them have a new list. If you look at the first one chmod function, first value is file_to_perm&&perm_number, these are two argv which must be separated with &&
The program will ask for an input parameter for file_to_perm and perm_number to the user, and append inputs to an array. Then the program will pass them to function. There is a rule: function must be in lib/generator/os_name/function_name.py and it will import in the program. Function name and file name must be same. And to get argv, your module must have a function name call run.
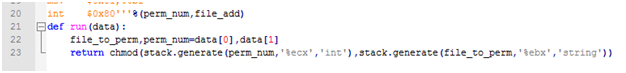
Exactly same chmod function in lib/generator/linux_x86/chmod.py
Data have two argv which is file_to_perm and perm_number given from user. After that you can do anything you want as well.
Now we going back to core/command.py for shellcode type. your module must have an encode type at least which is call none . you have to put shellcode encode types in to an array same as in core/command.py for chmod function.
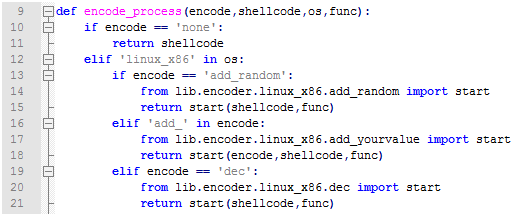
In the core/encode.py you can add your os name, shellcode type and if it’s none, there is no need to add anything! Shellcode will return without any changes.
With adding if/elif you can import your shellcode encoder and return it to software, to have a sorting rule please add your encoders to lib/encoder/os_name/encode_name.py with start function inside. You have encode , original shellcode, os name,function name, in software input with given by user. You can use them if you need them in your encoders!
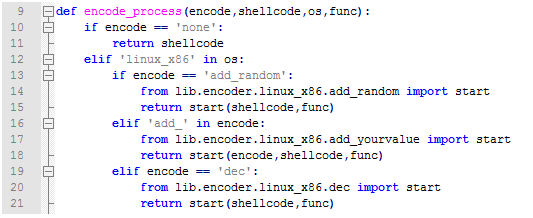
And here is a sample of start function. Remember to return the shellcode in end of your function.
Note: by adding your os/function/encode module in core/command.py, they will be list in software automatically for users.
Now if you want to add any OS, here is the structure and just separate os names with , to the core/command.py. If you need any extra changes , you can have it in core/run.py.
Here is a sample of adding new in command section.[line 46]
REMEMBER, all generator module must generate assembly codes, and then you have to forward them to opcoder and convert them to opcodes [shellcodes].
Software will forward the codes to core/opcoder.py
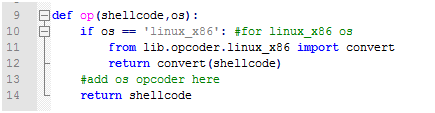
If you adding new os, you have to locate your file in lib/opcoder/os_name.py, which must have a convert function, with an input [for assembly code] and return value is shellcode[opcodes].
You can get opcodes from objdump in your computer on your OS and add the assembly codes with opcodes to your file, and then use replace() to replace them with opcodes, same as lib/opcoder/linux_x86.py. if you adding a new linux_x86 shellcode with or encode, you have to check that, assembly codes turn to shellcode all success and if it’s not, you can have an edit on this file.
replace_values_static array in linux_x86.py at line 13 is for static values! Same as xor %ebx,%ebx which in linux_x86 is always 31 db and you can find it with simple object dumping and adding it in array. For other dynamic opcodes same as mov $0x9043235f,%ebx which value sometimes is dynamic in hex, you can add a if or elif in line 84 and next… user input. Just remember don’t collision any OS with the other OS, they are all different!
And the last thing is about core/stack.py. this file can be useful in several ways.
- When you want to convert opcodes to shellcode and adding
\xto every hex/opcode with using shellcoder(shellcode) function. - st(data) function is useful to reverse the content , just like as stack structure. If you insert input like
/etc/passwdit will returndwssap/cte/ - generate(data,register,gtype) is the most useful. If you have a data which you need to send it to stack, to grab it from esp or grap part of it using pop, you have to send your data to this, data is the value which you want send it to stack. Like
/etc/passwd, register value should be a register name that can use if needed to shr or shl [shift right,shift left] to remove an extra useless char, which filled for remove NULLs\x00from shellcode. It’s something like a tmp register! And gtype is type of your input, if your data is string , you have to put it equal tostringand if it’s an integer you have to put it equal toint. example: generate(/etc/passwd,ebx,string) or generate(777,ecx,int). this function is useful for linux_x86 mostly and please use 32bit registers until it will be develop for more!